In this blog post we will talk about how to approach NSX manager certificate expiry issue.
NSX manager uses certificates for various purposes. You can check certificates from NSX manager UI.
System > Certificates
Following are commonly listed certificates in UI and their usage –
- APH-AR certificate – Used for inter-site communication using the AR channel (Async-Replicator channel)
- GlobalManager – PI certificate for the Global Manager
- mp-cluster certificate – Used for UI/API communication with the VIP of the Global Manager or Local Manager cluster
- tomcat certificate – Used for UI/API communication with individual Global Manager and Local Manager nodes for each of the locations added to the Global Manager .
- LocalManager – PI certificate for this specific Local Manager.
These certificates can se self-signed or CA signed certificates. By default, the certificates are self-signed. Whenever the certificate expires it raises and alarm.
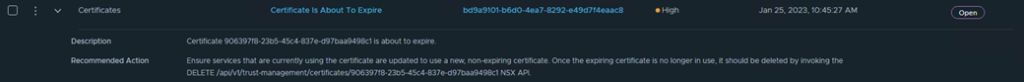
Before proceeding with certificate replacement, it is important to check whether the certificate is in use. The alert is generated even when the expiring certificate is not in use.
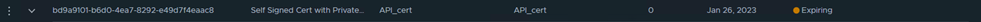
In NSX versions starting 3.2 UI includes an option to check where the certificate is being used. Here is an example,


This screenshot is from NSX manager version 4.0, we can see there is a column where used and it should 1 as value. If we click on 1 it will tell us where that certificate is being used.
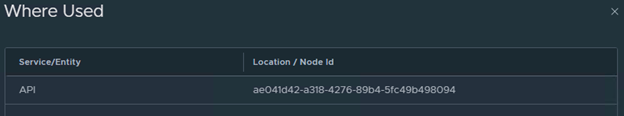
We can see this is API certificate being used by the manager node. The UUID belongs to NSX manager.
In versions prior to 3.2 UI does not have this option. For older versions we can leverage API to check whether a certificate is in use.
Refer to following link for steps to use Python and cURL with NSX manger https://clitoapi.com/2022/10/interact-with-vmware-nsx-using-manual-and-programmatic-methods/
We can use the following API,
GET https://<nsx-mngr> /api/v1/trust-management/certificates/<certificate-id>
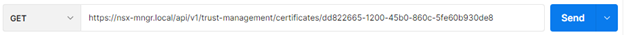
Let’s look at the response. We can see “resource_type”: “certificate_self_signed” and “used_by” field mentions node ID and service_type API.

Let’s try the same steps for a certificate that is not in use.
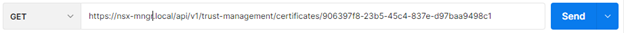
Let’s check the response here. We can see “resource_type”: “certificate_self_signed” but “used_by” field is blank.
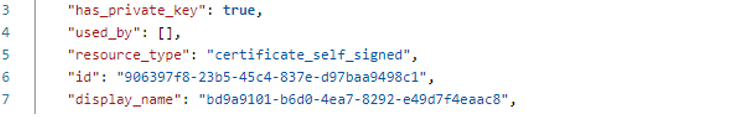
This means that the certificate is not in use.
As mentioned earlier starting from version 3.2 we can see this in UI.
You can use POSTMAN and refer to steps here in administration guide to replace certificates.